I am officially declaring 2017 the year of threat.

Doing my best to play the part of threat actor.( Defcon Tinfoil-Hat-Contest).
Following years of rhetoric about state-based attacks and who is at fault for what major system compromise the public seems to finally have come to grips with a few indisputable notes us security pros have been screaming at the tops of our lungs for a couple decades.
There is (at least) a threat out there targeting every principal.
The bad things threat actors cause mean more to the average person than the increasing the frequency of plastic rotation in a wallet.
Things are obviously getting worse.
The public hasn’t grokked this one yet but:
4. Things are trending to get very much worse before they can get better.
Other people publish lists of notable cyber loss events [1]. … and APTs … because they’re a thing [2].
It’s worth noting however there seems to be plenty of evidence materializing to back up the stupendous industry reports claiming an exploding threatscape.
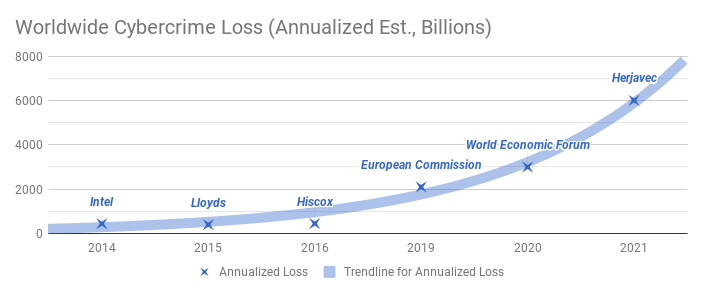
How has the security community collectively responded to the challenge that is threat?
Threat Intelligence

This experiment on the Blackhat floor (which is research worth doing) to find out what goes on at these conferences seems to reflect the industry sentiment of “stick a sensor on it”. Well, I did a booth audit at Blackhat US 2017 this year (in addition to my modus operandi of rag reading) to stick my own sensor in the industry.
Following well worn paths in meatspace, the security community (and no thanks to overtures from our politicians when they unilaterally try to “do something” about security without community feedback [Wassenaar]) has apparently given up on a common
shared defensive posture of the digital realm. I see continued talk in public about information sharing, but despite this the threat intelligence business has balkanized into a federated network of secret databases on who is doing what to whom and who has what from which places and who has what capabilities to do what to whom.
I haven’t named names here … but if you’re looking for threat intelligence to help you defend your network man do I have a bridge to sell you.
Active Threat Product Hunting
I audited every booth (well over 100) on the main floor (and I have as a consequence another email account you may have trouble reaching me at).
Believe it or not, I let every sales team give me the elevator. With few exceptions thats’ all many were worth.
I had lengthy conversations with over half of the vendors.
What did I learn?
Apparently most of that fresh security VC money [3] was dumped on shops who heroically think this thing called cybersec is going to be solved with saber wielding cyber warriors kitted out with tripwires and sensors and heads up displays (okay, the hololens thing at least had a cool factor) hunting threats stalking helpless press on enterprise networks. This despite the fact the enterprise network is quickly evaporating as endpoints get dumber and applications move onto third party networks.
It’s true that if you dump enough money on it more intelligence allows cybersec and infosec pros to make prescient minority-report style observations and maybe your firewalls can think for you too.
However if there is one truism I garnered it was that the solution landscape is just as technically difficult to navigate as the threat landscape and that the “machine intelligence” solutions all require superhuman intelligence to deploy.
I guess that means hire more infosec gurus? Oh yeah … there aren’t any more. [4]
So, you’ve got yourself a mythical infosec pro.
Despite 25% of infosec positions remaining unfilled and the labor market being overpriced and big game hunters have given up poaching to capture cyber warriors in the wild …. you captured yourself a unicorn or five (or maybe 10? lots of this threat hunting stuff looks like it takes work).
Do your security pros have the juice to actually force stakeholders to react at the speed of real time threats?
Does your organization have a rational resource allocation based on quantified or qualified risks?
Of course my observation has been that only small organizations are nimble. In large organizations being big just means falling harder (not being more rational).
In an industry that’s supposed to be based on methodical evaluation of security economics how did we end up with market solutions so out of balance with what can solve for outcomes?
Shouts out to evident.io with their risk based view of organizational cyber vulnerabilities, and I grok what both Upguard and Threatstack are building. There are others, I’m not the only one who gets it; but there’s not enough of us.
Threat firms out of touch with threatscape implications.
I believe their intelligence and tooling is impressive, but the economics of the situation are that we should be spending where we can be most effective first. Very few firms seem focused on delivering feedback to management which can inform the risk management process so it can fill strategic holes.
Most organizations need more strategy and an effective balanced deployment of contemporary security controls (which together can eliminate most risk).
Why do I see threat firms selling the idea of literally enabling counter-attack against cyber threat (and the US congress is making this legal)[5] when they should be helping organizational stakeholders improve ready-state posturing?
So what should we do about cyber?
(Yes, this seems to be the mainstream parlance. No pointing in making a stand here.)
Yes I know strategic posturing is mostly the remit of consulting engagements and CISO planning and big thick paper reports that sit around collecting exactly a year of dust.
But why?
I’m focusing on helping businesses improve outcomes and this might just mean augmented reality, machine learning and cyber-acrobatics don’t take a front seat.
[1] "Significant Cyber Incidents", Csis.org, 2017. [Online]. Available: https://www.csis.org/programs/cybersecurity-and-warfare/technology-policy-program/other-projects-cybersecurity. [Accessed: 14- Dec- 2017]. [2] "the list of publicly reported groups tracked in ATT&CK", Attack.mitre.org, 2017. [Online]. Available: https://attack.mitre.org/wiki/Groups. [Accessed: 14- Dec- 2017]. [3] M. Chapman, "VC Firms Back Record Number of Cybersecurity Startups in 2016", Bloomberg.com, 2017. [Online]. Available: https://www.bloomberg.com/news/articles/2017-02-08/vc-firms-back-record-number-of-cybersecurity-startups-in-2016. [Accessed: 14- Dec- 2017]. [4] "Cybersecurity Unemployment Rate, Jobs and Statistics", Cybersecurity Ventures, 2017. [Online]. Available: https://cybersecurityventures.com/cybersecurity-unemployment-rate/. [Accessed: 13- Dec- 2017]. [5] J. Wolff, "Oh Good, the Worst Idea in Cybersecurity Is Back Again", Slate Magazine, 2017. [Online]. Available: http://www.slate.com/articles/technology/future_tense/2017/10/hacking_back_the_worst_idea_in_cybersecurity_rises_again.html. [Accessed: 14- Dec- 2017].



