Okay, so this shouldn’t be news to anyone moderately concerned with the safety of their personal information or corporate resources, but this week reinforced a growing trend in information systems:
The web-browser is the largest attack vector on any platform.
This week saw one disclosure and two separate 0-day attacks which left nowhere to hide on the web.
Pwn2Own Mobile 2012
The Pwn2Own Mobile, an annual contest which pits the latest security on dominant mobile platforms against determined hackers. The contest rarely leaves anyone standing, but all software vendors aspire to an undefeated status (if they can boast for only a week before the next round of patching).
A WebKit vulnerability was used to plow through all security layers on both iOS 5.1.1 and iOS 6 on the iPhone 4S. The timing of the attack means the iPhone 5 due for release tomorrow will not be patched prior to hitting the streets.
Joost Pol and Daan Keuper of Certified Secure demonstrated the attack which they created from scratch during after work hours in just a few weeks
In an interview Pol was quoted as saying:
“The easy part was finding the WebKit zero-day. It was a basic vulnerability but we had to chain a lot of things together to write the exploit.”
Pol left the interview with the warning:
“The CEO of a company should never be doing e-mail or anything of value on an iPhone or a BlackBerry. It’s simple as that. There are a lot of people taking photos on their phones that they shouldn’t be taking.“
The 0-day vulnerability used in this attack was found in the WebKit framework utilized as the basis for Google’s Chrome and Android Browsers, Apple’s Safari and iOS Browsers, as well as the latest RIM Blackberry (among others).
Demonstrated attacks on these platforms were beyond the scope of the contest, and the exploit code was destroyed following the event however the details of the vulnerability were disclosed to affected software vendors for patching.
Internet Explorer & Flash Mayhem …. Part XXVII
This week security firm Rapid7 announced they had discovered a 0-day Internet Explorer drive-by exploit in the wild which poses as flash code to obtain logged-in user privileges. Adobe is off the hook this time as the exploit does not depend on a vulnerability in the flash-plugin itself.
The exploit works across the entire family of currently supported browsers from Microsoft including Internet Explorer7, 8 and 9 running on Windows XP, Windows Vista, and Windows 7.
A patch has yet to be delivered however Microsoft has promised it tomorrow.The black-hat gang responsible for this exploit — Nitro — was also responsible for the recent Java exploit which forced Oracle to abandon it’s conservative patch cycle as it scrambled to reassure enterprise customers.
CRIME follows BEAST
Juliano Rizzo and Thai Duong who last year demonstrated BEAST — a high-profile attack on the TLS protocol this year again cracked SSL through an information-disclosure design flaw which affected several browsers from Mozilla and Google (and others who implemented SSL/TLS compression with SPDY).
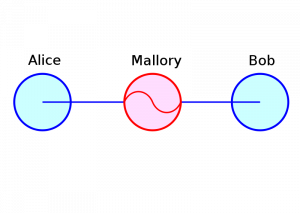
Man-In-The-Middle, Attribution: cs:Wikipedista:Miraceti
Their CRIME exploit allows a nefarious attacker to hijack a web session utilizing a man-in-the-middle approach (this is what SSL is designed to prevent) if the victim’s browser has implemented the latest compression standards for SSL. This can for example be executed on a local wireless network.
Mozilla and Google who were given advance notice of the attack had already released patches, however when I audited for the impact on my own client systems I determined patch uptake was insufficient and I was forced to use a server-side workaround to disable SSL protocol compression.
More Ammunition for the Defense in Depth Argument
I was not surprised by any of this week’s events however it made for convenient timing to highlight a point I make with all of my clients. Perimeter security is poor security, defense in depth is required, and this means you.
I like to see the web blocked completely from secure networks, with user desktops treated as hostile territory regardless of their owners titles or job functions.





